"Fighting
for the
USER"
Digital Parsing
Whenever I saw an
"injustice"
I would create
"unique things"
to
"Balance the Equation"
with
Research, Analysis, and Developments
Happy, Happy, Joy, Joy
:)

Lamentably...
As with most of my
POC's, heutagogical R&D, TOADDs, or Tech,
once I would see a calamitous or foreseeable (potential) abuse
in "real world" entanglement(s)...,
they were all abruptly
terminated
and
buried
within the
"Ark of the Covenant" ...
for
"Embedded Journalists"
(2005-2013)
For over seven years
I gave Journalists the ability to
report and send Text and Images
during civil unrest, from within blocked, restricted,
or Geo-restricted areas or countries like:
the Gaza Strip,
Homs Syria,
China,
Turkey,
etc.;
all by simply using
"Frequency Jumping"-not reliant on WiFi/Cell
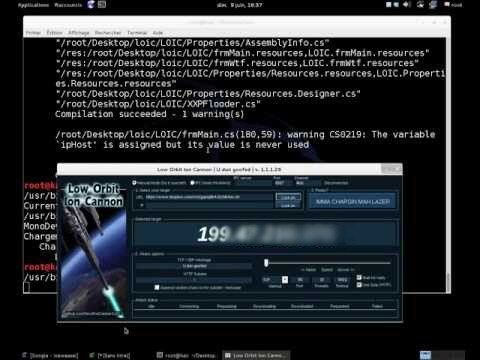
and segmental modified LOIC & JS LOIC hack/techniques...
" Noʻu ka hauʻoli "
World! :)
(circa 2010-2012)
It was in initially a "POC" - proof-of-concept that combined software and hardware (portable encrypted USB) to enforce "Secure Transfer Protocols" on a computer's network, connected servers, and to evade MITM over the internet (which was severely lacking in browsing between 2000-2014) and later employed testing fingerprinting protocols to validate websites and secure privacy while transferring digital data over the internet (2008-2014).
After a few years, I made a "Tijuana water-downed" version which I loaded onto a Military grade Secure Key FIPS 140-2 Level 3 Validated 256-bit Encryption USB, that also contained a simple UI (User Interface), and placed it on Kickstarter as
(circa 2013-2014)
" Noʻu ka hauʻoli "
World! :)